The Power of Intel Platform Trust Technology
Intel Platform Trust Technology (PTT) is a crucial component in modern computing systems that enhances security and trustworthiness. As cyber threats continue to evolve, it is essential for hardware manufacturers to implement robust security features to protect sensitive data and ensure system integrity.
PTT is integrated into Intel processors and chipsets, providing a foundation for secure boot, measured boot, and trusted execution environments. By leveraging hardware-based security mechanisms, PTT helps prevent unauthorized access to critical system resources and mitigates the risk of malware attacks.
One of the key features of Intel PTT is its support for Trusted Platform Module (TPM) functionality. TPM is a specialized hardware component that stores cryptographic keys, certificates, and other sensitive information securely. By utilizing TPM through Intel PTT, users can encrypt data, authenticate devices, and establish secure communication channels.
Furthermore, Intel PTT enables secure attestation, which allows systems to prove their identity and integrity to external entities. This feature is particularly valuable in enterprise environments where trustworthiness and compliance are paramount.
Overall, Intel Platform Trust Technology plays a vital role in strengthening the security posture of modern computing platforms. By incorporating hardware-based security measures at the foundational level, Intel PTT helps safeguard data confidentiality, integrity, and availability.
As cyber threats continue to pose significant risks to organizations and individuals alike, technologies like Intel PTT are instrumental in building resilient defense mechanisms against malicious actors. Embracing hardware-based security solutions is essential in today’s digital landscape to ensure safe and reliable computing experiences.
Top 5 Frequently Asked Questions About Enabling and Using Intel Platform Trust Technology
- How do I enable or disable Intel platform trust technology?
- What happens when you enable Intel PTT?
- What is Intel trust platform?
- Should I enable PTT in BIOS?
- Should I enable trusted platform module?
How do I enable or disable Intel platform trust technology?
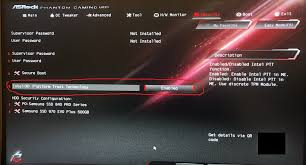
Enabling or disabling Intel Platform Trust Technology (PTT) typically involves accessing the BIOS or UEFI settings of your computer’s motherboard. To enable PTT, you would need to enter the BIOS/UEFI setup utility during the system boot process and navigate to the Security or Advanced tab where you can find the PTT setting. From there, you can usually toggle the PTT option to enable it. Conversely, to disable PTT, you would follow a similar process in the BIOS/UEFI settings and switch off the PTT feature. It’s important to note that specific steps may vary depending on your computer’s manufacturer and model, so consulting the user manual or contacting technical support for guidance is recommended if you encounter any difficulties in managing Intel PTT settings.
What happens when you enable Intel PTT?
When you enable Intel Platform Trust Technology (PTT), your system gains an added layer of security through hardware-based mechanisms integrated into Intel processors and chipsets. By activating Intel PTT, you initiate a secure environment that supports features such as secure boot, measured boot, and trusted execution. This means that sensitive data is better protected, unauthorized access is mitigated, and the risk of malware attacks is reduced. Additionally, enabling Intel PTT allows for the utilization of Trusted Platform Module (TPM) functionality, enabling encryption of data, authentication of devices, and establishment of secure communication channels. In essence, enabling Intel PTT enhances the security posture of your system by leveraging hardware-based security measures to safeguard critical resources and ensure the integrity of your computing environment.
What is Intel trust platform?
Intel Platform Trust Technology (PTT) is a security feature integrated into Intel processors and chipsets to enhance system security and trustworthiness. Essentially, Intel PTT leverages hardware-based security mechanisms to provide a foundation for secure boot, measured boot, and trusted execution environments. It works in conjunction with Trusted Platform Module (TPM) functionality to securely store cryptographic keys, certificates, and sensitive data. By utilizing Intel PTT, users can encrypt data, authenticate devices, establish secure communication channels, and prove system identity and integrity through secure attestation. In essence, Intel Platform Trust Technology plays a crucial role in fortifying the security posture of computing systems by implementing robust hardware-based security measures.
Should I enable PTT in BIOS?
Enabling Intel Platform Trust Technology (PTT) in BIOS is a common query among users seeking to enhance the security of their systems. The decision to enable PTT depends on individual security needs and the specific features and functionalities desired. By enabling PTT, users can leverage hardware-based security mechanisms to strengthen system integrity, protect sensitive data, and establish secure communication channels. However, it is crucial to understand the implications of enabling PTT, such as potential compatibility issues with certain applications or services. Users should weigh the benefits of enhanced security against any potential drawbacks before making an informed decision on whether to enable PTT in BIOS settings.
Should I enable trusted platform module?
Enabling the Trusted Platform Module (TPM) is highly recommended for enhancing the security of your system, especially when it comes to utilizing Intel Platform Trust Technology (PTT). TPM provides a secure hardware-based environment for storing sensitive data, cryptographic keys, and ensuring secure boot processes. By enabling TPM, you can strengthen data encryption, device authentication, and overall system integrity. This added layer of security helps protect against unauthorized access and mitigates the risk of cyber threats. Therefore, enabling TPM is a proactive step towards bolstering the security of your computing environment and safeguarding your valuable information.
Tags: authentication, encryption, hardware-based security, intel platform trust technology, measured boot, ptt, secure attestation, secure boot, secure communication channels, security, tpm, trusted execution environments, trusted platform module